 The main purpose of VPN and Proxy is to provide a connection between the host computer and the remote computer by hiding host computer’s IP to make it secure against intruders.
The main purpose of VPN and Proxy is to provide a connection between the host computer and the remote computer by hiding host computer’s IP to make it secure against intruders.
The basic difference between VPN and Proxy is that a Proxy server allows to hide, conceal and make your network id anonymous by hiding your IP address. It provides features like Firewall and network data filtering, network connection sharing and Data caching. This first became popular where some countries tried to limit their citizen’s Internet access.
On the other hand, a VPN has benefits over the proxy by creating a tunnel over the public Internet between computers or hosts. A tunnel is formed by the encapsulation of the packets by any encryption protocol.
Encryption protocol such as Open VPN, IPsec, PPTP, L2TP, SSL and TLS, encrypts the data and adds a new header. This has helped companies to minimize the expenditures of leased lines and the high-speed routing services of the public internet to transfer data more securely.
Content: VPN Vs Proxy
Comparison Chart
| Basis for comparison | VPN | Proxy |
|---|---|---|
| Security | Provides encryption, authentication and integrity protection to the traffic. | It does not provide any type of security. |
| Works on | Firewall | Browsers |
| Tunnel creation | A secure link is created between the end users. | Tunnel formation does not take place. |
| Protocols used | PTTP, L2TP, IPsec, etc. | HTTP, TELNET, SMTP, and FTP. |
Definition of VPN
A VPN (Virtual Private Network) is an encrypted connection between private networks and a public network, similar to the internet. The V stands for Virtual, and N stands for network. The information from a private network is securely transported to a public network. This virtual connection is made up of packets.
VPN creates a network which is physically public but virtually private. The network is private because it ensures the organization privacy internally and virtual since it does not use actual private WANs. In addition, Virtual Private Network provides a mechanism for employing authentication, integrity protection including encryption.
VPN provides a highly secured connection, however, it does not need any specific cabling in the interest of the organization that wants to use it. Therefore, a VPN merges the benefits of a public network (cheap and easily available) with those of a private network (secure and reliable).
How a VPN works?
The idea of a VPN is easy to understand. Assume an organization has two networks, Network 1 and Network 2, which are physically separated from each other and we need to establish a connection between with them using the VPN concept. In such case, we install two firewalls, Firewall 1 and Firewall 2. Firewalls perform the encryption and decryption. Now, lets us understand how the VPN guard the traffic moving between any two hosts on the two different networks.
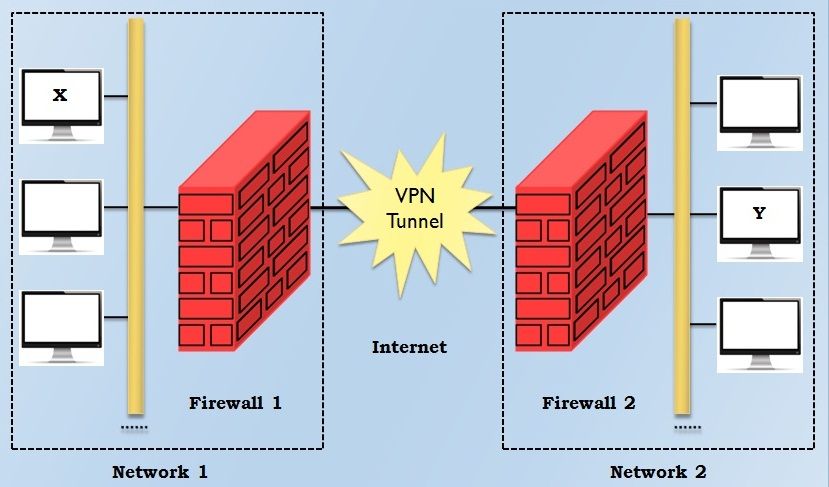 For this, suppose host X on Network 1 require to send a data packet to host Y on Network 2. This transmission would work as follows.
For this, suppose host X on Network 1 require to send a data packet to host Y on Network 2. This transmission would work as follows.
- Host X creates packets, inserts its own IP address as the source address and the IP address of host Y as the destination address.
- The packet reaches Firewall 1. Firewall 1 now adds new headers to the packet. In these recent headers, it modifies the packet’s source IP address to its own address from the host X. It also changes the destination IP address of the packet from that of host Y to the IP address of Firewall 2. It also carries out the packet encryption and authentication, depending on the settings and sends the modified packet over the Internet.
- The packet reaches Firewall 2 over the Internet, via one or more routers, as usual. Firewall 2 drops the outer header and performs the appropriate decryption and other cryptographic function as necessary. This obtains the original packet, as was constructed by host X in Step 1. Then it observes at the plain text contents of the packet and realizes that the packet is meant for host Y. Thus, it delivers the packet to host Y.
Definition of Proxy
A proxy server is a computer or software which behaves as an intermediary between the client and actual server. It usually hides the client’s IP and uses the anonymous network ID for connecting to the network. Proxy servers decide the flow of application traffic level and perform network data filtering, network connection sharing and data caching.
How a proxy servers works?
- An interior user communicates to the proxy server using a TCP/IP application, such as HTTP and Telnet.
- The proxy server asks the user about the remote host with which the user required to establish a link for the communication (i.e. its IP address or domain name, etc.). It also asks the user ID and password required to access the services of the proxy server.
- Then the user provides this information to the application gateway.
- Now the remote host is accessed by the proxy server on behalf of the user and transfers the packets of the user to the remote host.
Proxy servers are highly secured as compared to packet filters. Its reason is that here we simply detect whether a user is allowed to work with a TCP/IP application or not instead of examining every packet against several rules. The demerit of a proxy server is the overhead regarding the number of connections.
Key Differences Between VPN and Proxy
- VPN provides encryption, authentication and integrity protection to the traffic whereas Proxy doesn’t provide much security over the connection.
- Proxy functions at browsers while VPN functions at the firewall.
- VPN creates a tunnel for connecting two systems firewall. As against, a proxy doesn’t create any tunnel.
- The proxy uses protocols like HTTP, TELNET, SMTP and FTP. In contrast, VPN uses protocols such as PTTP, L2TP, IPsec, etc.
Conclusion
Both VPN and Proxy serves almost the same purpose, but a VPN provides more security than a proxy server.
Neha Patel says
Your website is beneficial for me….. very elaborated contents….