 Substitution technique and transposition technique are the fundamental methods of codifying the plaintext message to acquire the respective ciphertext. These two methods are the basic building blocks of the encryption techniques and can also be used together, which is called a product cipher.
Substitution technique and transposition technique are the fundamental methods of codifying the plaintext message to acquire the respective ciphertext. These two methods are the basic building blocks of the encryption techniques and can also be used together, which is called a product cipher.
The essential difference between the substitution technique and transpositional technique is that the substitution technique substitutes the letters of the plaintext from other letters, number and symbols. On the other hand, the transposition techniques do not replace the letter, instead changes the position of the symbol.
Content: Substitution Technique Vs Transposition Technique
Comparison Chart
| Basis for comparison | Substitution Technique | Transposition Technique |
|---|---|---|
| Basic | Replaces the plaintext characters with other characters, numbers and symbols. | Rearranges the position of the characters of the plaintext. |
| Forms | Monoalphabetic and polyalphabetic substitution cipher. | Keyless and keyed transpositional cipher. |
| Alterations | The identity of the character is changed while its position remains unchanged. | The position of the character is changed in spite of its identity. |
| Demerit | The letter with the low frequency can discern the plaintext. | Keys near to the correct key can disclose the plaintext. |
| Example | Caesar Cipher | Reil Fence Cipher |
Definition of Substitution Technique
Substitution technique involves the replacement of the letters by other letters and symbols. In a more straightforward way, the characters of plaintext are replaced, and other substitute characters, numbers and symbols are used at their place. Caesar cipher uses the substitution technique where the alphabets are replaced with the other alphabets which are three position forward of the line. Julius Caesar devised this technique, and it was named after him as the Caesar Cipher. For example, the plaintext “HOPE” will be converted into “KRSH” using Caesar Cipher. There are several substitution techniques are developed after caesar cipher such as Mono-alphabetic cipher, Homophobic substitution cipher, Polygram substitution cipher, Polyalphabetic substitution cipher, Playfair cipher and Hill cipher.
The Caesar cipher was the weakest cipher, although the evolution of the techniques made the new version stronger. The limitation of the substitution technique is that it is very predictable if the translation table is known the substitution can be broken.
Definition of Transposition Technique
In transposition technique, the identity of the characters remains unchanged, but their positions are changed to create the ciphertext. The transposition technique is illustrated in the example given below. Here we have modified four lines of text with the help of transpositional cipher. The two-dimensional matrix are used to organise the characters and columns are swapped according to the key. The key is used to specify which columns have to be interchanged. Following the key as shown in the figure, the alphabet column number 1 is swapped to column number 3, and the alphabets of the column number 2 is swapped to the column number 6. 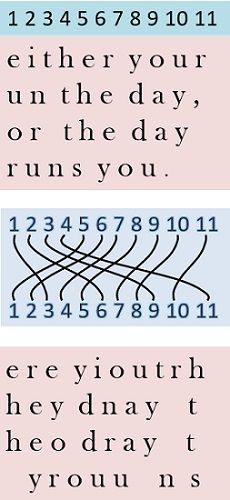 In a similar way, other columns are also swapped. The examples of transposition technique are Rail fence technique, Simple columnar, Vernam cipher and Book cipher.
In a similar way, other columns are also swapped. The examples of transposition technique are Rail fence technique, Simple columnar, Vernam cipher and Book cipher.
To decrypt the ciphertext into the plaintext, the reverse process has to be followed. The transposition technique is not considered as to be a very secure method. The plaintext can easily be discovered by using hit and trial method and carefully observing the frequency of the characters and the characteristic patterns of pairs of consecutive letters (known as digrams and trigrams for the group of 2 and 3 letters respectively).
Key Differences Between Substitution Technique and Transposition Technique
- The substitution technique uses a substitute for the plaintext characters to convert it into ciphertext. On the other hand, the transposition technique basically rearranges the characters of the plaintext.
- Monoalphabetic, polyalphabetic substitution cipher, Playfair cipher are some of the algorithms which use the substitution technique. As against, the forms of transposition technique are keyed and keyless transpositional cipher.
- The substitution technique aims to alter the identity of the entity while the transposition technique alters the position of the entity, rather than its identity.
- With the help of the low-frequency letter, the plaintext can be easily discerned in the substitution technique. On the contrary, in the transposition technique, the keys near to the right key lead to the detection of the plaintext.
Conclusion
The substitution and transposition techniques are used for converting a plaintext into ciphertext, where substitution technique replaces the characters whereas transposition technique rearranges the characters to form a ciphertext. However, a substitution cipher is simpler and easy to break.
Leave a Reply