 The major difference between active and passive attacks is that in active attacks the attacker intercepts the connection and modifies the information. Whereas, in a passive attack, the attacker intercepts the transit information with the intention of reading and analyzing the information not for altering it.
The major difference between active and passive attacks is that in active attacks the attacker intercepts the connection and modifies the information. Whereas, in a passive attack, the attacker intercepts the transit information with the intention of reading and analyzing the information not for altering it.
There are various types of threats, attacks and vulnerabilities present to corrupt and breach the system security. Security attacks are the computer attacks that compromise the security of the system. Conceptually, the security attacks can be classified into two types that are active and passive attacks where the attacker gains illegal access to the system’s resources.
Content: Active Attacks Vs Passive Attacks
Comparison Chart
| Basis for comparison | Active Attack | Passive Attack |
|---|---|---|
| Basic | Active attack tries to change the system resources or affect their operation. | Passive attack tries to read or make use of information from the system but does not influence system resources. |
| Modification in the information | Occurs | does not take place |
| Harm to the system | Always causes damage to the system. | Do not cause any harm. |
| Threat to | Integrity and availability | Confidentiality |
| Attack awareness | The entity (victim) gets informed about the attack. | The entity is unaware of the attack. |
| Task performed by the attacker | The transmission is captured by physically controlling the portion of a link. | Just need to observe the transmission. |
| Emphasis is on | Detection | Prevention |
Definition of Active Attacks
Active attacks are the attacks in which the attacker tries to modify the information or creates a false message. The prevention of these attacks is quite difficult because of a broad range of potential physical, network and software vulnerabilities. Instead of prevention, it emphasizes on the detection of the attack and recovery from any disruption or delay caused by it. 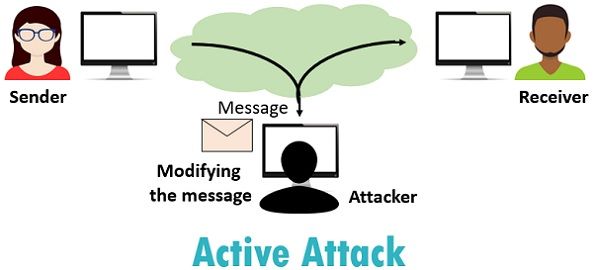 An active attack usually requires more effort and often more dangerous implication. When the hacker attempts to attack, the victim gets aware of it.
An active attack usually requires more effort and often more dangerous implication. When the hacker attempts to attack, the victim gets aware of it.
The active attacks are in the form of interruption, modification and fabrication.
- Interruption is known as masquerade attack in which unauthorized attacker tries to pose as another entity.
- Modification can be done using two ways replay attack and alteration. In the replay attack, a sequence of events or some data units is captured and resent by them. While alteration of the message involves some change to the original message, either one of them can cause alteration.
- Fabrication causes Denial Of Service (DOS) attacks in which attacker strive to prevent licit users from accessing some services, which they are permitted to or in simple words the attacker gain access to the network and then lock the authorized user out.
Definition of Passive Attacks
Passive attacks are the attacks where the attacker indulges in unauthorized eavesdropping, just monitoring the transmission or gathering information. The eavesdropper does not make any changes to the data or the system.
Unlike active attack, the passive attack is hard to detect because it doesn’t involve any alteration in the data or system resources. Thus, the attacked entity doesn’t get any clue about the attack. Although, it can be prevented using encryption methods in which the data is firstly encoded in the unintelligible language at the sender’s end and then at the receivers end it is again converted into human understandable language. 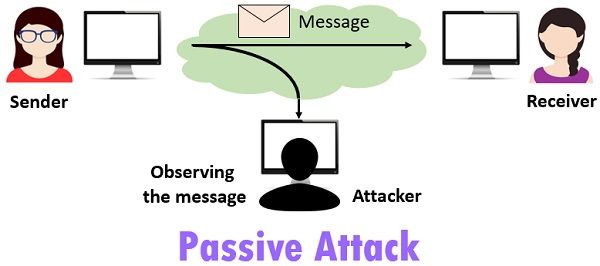 In this way, at the time of transit, the message is in an unintelligible form which could not be understood by the hackers. That is the reason, in passive attacks, the prevention has more concern than detection. The passive attacks entangle the open ports that are not protected by firewalls. The attacker continuously searches for the vulnerabilities and once it is found the attacker gains access to network and system.
In this way, at the time of transit, the message is in an unintelligible form which could not be understood by the hackers. That is the reason, in passive attacks, the prevention has more concern than detection. The passive attacks entangle the open ports that are not protected by firewalls. The attacker continuously searches for the vulnerabilities and once it is found the attacker gains access to network and system.
The passive attacks are further classified into two types, first is the release of message content and second is traffic analysis.
- The release of message content can be expressed with an example, in which the sender wants to send a confidential message or email to the receiver. The sender doesn’t want the contents of that message to be read by some interceptor.
- By using encryption a message could be masked in order to prevent the extraction of the information from the message, even if the message is captured. Though still attacker can analyse the traffic and observe the pattern to retrieve the information. This type of passive attack refers to as traffic analysis.
Key Differences Between Active and Passive Attacks
- The active attack includes modification of the message. On the other hand, in passive attacks, the attacker doesn’t commit any changes to the intercepted information.
- The active attack causes a huge amount of harm to the system while the passive attack doesn’t cause any harm to the system resources.
- A passive attack is considered as a threat to data confidentiality. In contrast, an active attack is a threat to the integrity and availability of the data.
- The attacked entity is aware of the attack in case of active attack. As against, the victim is unaware of the attack in the passive attack.
- The active attack is accomplished by gaining the physical control over the communication link to capture and insert transmission. On the contrary, in a passive attack, the attacker just needs to observe the transmission.
Conclusion
The active and passive attacks can be differentiated on the basis of what are they, how they are performed and how much extent of damage they cause to the system resources. But, majorly the active attack modifies the information and causes a lot of damage to the system resources and can affect its operation. Conversely, the passive attack does not make any changes to the system resources and therefore doesn’t causes any damage.
KHABA says
Nice article lucid explanation…
dragonse says
Clearly explained. Thank you
sethupathy says
good information.
smith john says
nice content, easy to read…. awesome information.. 🙂
Diksha says
Contents are in understandable format.
Very useful information.
Thank You. 🙂
ebin games says
Great explanation!!
Krunal says
Nice article, keep it UP
Fayzan Bhatti says
Got proper difference thanks….!